BLOG
Barrie After Dark: Food, Drinks, and Adult Entertainment

Barrie might be known for its waterfront and ski trips, but after dark the city has a social side that surprises a lot of visitors. Whether you are in town for a weekend getaway, a business trip, or a celebration with friends, there are plenty of ways to enjoy Barrie’s nightlife in a fun, relaxed, and adult-oriented way.
Here is a practical look at what a night out in Barrie can include, plus a few tips to help you plan responsibly.
Start with Food and Drinks
A good night usually begins with a solid meal. Downtown Barrie has a strong mix of casual and upscale spots where you can settle in before heading out.
You will find:
- Craft beer bars with local Ontario brews
- Cocktail lounges with a more intimate feel
- Steakhouses and late-night kitchens that stay open past the usual dinner hours
Choosing a place close to Dunlop Street or the waterfront makes it easy to walk between venues later in the evening.
Bars, Lounges, and Late-Night Vibes
TheRedZone Barrie’s bar scene covers a wide range of moods. Some places focus on dancing and DJs, while others are better for conversation and drinks in a quieter setting.
Popular nightlife experiences in Barrie include:
- Dance clubs that get busy on Friday and Saturday nights
- Sports bars where you can catch a game and hang out with a group
- Laid-back pubs that are ideal for a slower pace
If you are planning a birthday, bachelor party, or guys’ weekend, it is smart to map out two or three stops in advance so you are not wandering around trying to decide where to go next.
Adult Entertainment Options
For visitors looking for more private, adult-oriented experiences, Barrie also has discreet services that cater to consenting adults. These are typically arranged in advance rather than found by walking around nightlife districts.
Online directories are commonly used to browse profiles, check availability, and understand what type of experience is being offered. For example, some visitors look through listings for escort services in Barrie to explore companionship options while they are in town.
If you go this route, keep a few things in mind:
- Always communicate clearly and respectfully
- Understand the expectations and boundaries ahead of time
- Prioritize privacy and discretion for everyone involved
This part of the nightlife scene is more about planning than spontaneity, so it helps to do your research earlier in the day rather than late at night.
Plan Transportation Ahead of Time
One of the easiest ways to ruin a good night is by not thinking about how you will get home.
Barrie has taxis and rideshare options, but wait times can increase late at night, especially on weekends. If you are staying at a hotel, check whether they can call a cab for you or recommend reliable local drivers.
If you are with a group, consider:
- Booking a larger rideshare vehicle in advance
- Splitting into smaller groups with clear pickup points
- Staying within walking distance of your main venues
Being organized about transport keeps the night smooth and avoids unnecessary stress at the end.
Respect Local Rules and Boundaries
Ontario has specific laws around adult services, and venues also have their own house rules. Being a respectful guest in any setting goes a long way.
A few basic guidelines:
- Do not assume anything that has not been clearly agreed upon
- Avoid discussing private arrangements loudly in public venues
- Treat staff, performers, and companions with courtesy at all times
Discretion and respect are part of the culture around adult nightlife, and people who ignore that usually find themselves unwelcome quickly.
Make It a Night to Remember, Not Regret
A great night out in Barrie is about balance. Good food, a few drinks, fun venues, and, for some visitors, private adult companionship can all be part of the experience. The key is pacing yourself, planning ahead, and making choices you will feel comfortable about the next day.
BLOG
Wellness Travel for Women in Asia: From Phuket Spas to Korea’s Private Home Massage Services

Travel is not just about seeing new places anymore. For many women, it is also about how they feel while they are there. Rested. Safe. Taken care of. Across Asia, wellness has become a big part of the travel experience, and different countries offer their own approach to relaxation and self care.
Two places that show this contrast well are Thailand and South Korea. One is known for beachside spa culture. The other is building a reputation for privacy focused, women only wellness services. Both reflect a growing demand for comfort, trust, and personalized care.
Thailand: The Classic Spa Destination
Thailand has long been one of the world’s spa capitals. In places like Phuket, wellness is woven into the travel lifestyle. You will find everything from luxury resort spas to small neighborhood massage studios. Traditional Thai massage, herbal compress therapy, and aromatherapy oil treatments are widely available and relatively affordable.
For many women travelers, the appeal is simple. You can spend the morning at the beach and the afternoon in a spa overlooking the ocean. Resorts often design packages specifically for women, including detox programs, yoga sessions, and skin treatments. The atmosphere is open, social, and often set in beautiful surroundings.
But spa culture in Thailand usually means going out to receive treatment. Even in high end settings, you are still in a shared environment. For some women, that is part of the fun. For others, especially those who value privacy or feel tired after long travel days, going out again for a treatment can feel like extra effort.
South Korea: Privacy and Comfort First
South Korea’s wellness scene has grown in a different direction. While the country is known for public bathhouses and skincare clinics, there is also a rising demand for more private, women focused services. This is where home visit massage platforms come in.
Instead of traveling to a spa, the service comes to you. A trained therapist arrives at your home, hotel, or private accommodation with professional equipment and oils. The focus is usually on aromatherapy, stress relief, and therapeutic bodywork rather than the social spa experience.
Some services are designed specifically for women, with female therapists and women only policies to create a stronger sense of safety and ease. Platforms like 토닥이 specialize in this model, offering women only home visit aromatherapy and therapeutic massage services across South Korea. For many clients, the biggest benefit is being able to relax in a familiar, private space without worrying about crowded waiting areas or unfamiliar environments.
Why This Matters for Women Travelers
Women often think about wellness differently when they travel. Safety, privacy, and trust play a major role in deciding where and how to book a treatment. A beautiful spa setting is appealing, but so is the option to stay in your room, especially after a long flight or a full day of sightseeing.
There is also the emotional side of wellness. Travel can be exciting but also exhausting. Jet lag, walking all day, and adjusting to new environments can take a toll on the body. Having access to services that feel gentle, respectful, and tailored to women’s needs makes a real difference.
In Thailand, that might mean choosing a reputable spa with female therapists and private treatment rooms. In Korea, it might mean choosing a vetted home visit service where you control the environment completely.
Cultural Differences in Wellness
These two approaches also reflect cultural differences. Thailand’s tourism industry has long embraced hospitality in open, social settings. Spas are designed as destinations in themselves, places where guests gather, relax, and enjoy the atmosphere.
In South Korea, there is often a stronger emphasis on efficiency and personal space. Home visit services fit naturally into a lifestyle where convenience and privacy are highly valued. The idea of receiving professional care at home is not seen as unusual, but as a practical extension of modern wellness.
Neither approach is better. They simply meet different needs and preferences.
Choosing What’s Right for You
If you are planning a trip to Asia and want to include wellness in your plans, think about what helps you relax most.
Do you enjoy calming music, spa decor, and the feeling of being pampered in a dedicated space? A resort or day spa in Thailand might be perfect.
Do you prefer staying in your own space, wearing comfortable clothes, and not having to travel again after your treatment? A private home visit service in Korea may feel more comfortable.
Also consider timing. Early in a trip, a spa visit can help you unwind and get into vacation mode. Toward the end, when you are more tired, in-room or in-home services can be easier on your energy levels.
The Future of Women Focused Wellness
Across Asia, one clear trend is emerging. Women want more control over how they experience wellness. They are looking for services that respect their boundaries, understand their comfort levels, and adapt to their schedules.
Whether it is a seaside massage pavilion in Phuket or a private aromatherapy session in a Seoul apartment, the goal is the same. To feel safe. To feel cared for. To return home not just with photos, but with a body and mind that truly had a chance to rest.
BLOG
Night Out in Ulsan: Where 울산 풀사롱 Guides You

Ulsan isn’t just an industrial city—it also has a lively nightlife scene that attracts both locals and visitors looking for entertainment after dark. From karaoke bars to stylish lounges, there’s something for everyone.
For those interested in adult entertainment, websites like 울산 풀사롱 (ulsanfullsalon.org) offer guides and reviews of Ulsan’s top venues, including services from Korea, Thailand, and China. This makes it easier for visitors to plan a night out and find the best spots for karaoke, drinks, and socializing.
Top Nightlife Options in Ulsan
1. Karaoke Bars and Rooms
Karaoke is a staple of Ulsan’s evening entertainment. Private rooms allow groups to sing, relax, and enjoy drinks in a comfortable setting. Many venues provide themed rooms, high-quality sound systems, and a wide selection of songs in multiple languages.
2. Lounges and Bars
Ulsan has a variety of stylish bars and lounges where visitors can enjoy cocktails, socialize with friends, or meet locals. Happy hours and live music events make these spots perfect for a casual night out.
3. Entertainment Services
For those looking for a more specialized experience, some venues offer professional entertainment with hosts and performances. Websites like ulsanfullsalon.org provide detailed listings and reviews, helping visitors find trusted, high-quality venues.
Tips for Enjoying Ulsan’s Nightlife
- Plan ahead: Check online guides to find the best venues for your interests.
- Stay safe: Always go out with friends or in groups, and keep an eye on your belongings.
- Respect local customs: Understanding cultural etiquette ensures a smooth and enjoyable night.
- Try something new: Ulsan’s nightlife offers experiences you won’t find anywhere else, from unique karaoke setups to live performances.
Making the Most of Your Night Out
By planning your evening and using trusted resources, visitors can make the most of Ulsan’s vibrant nightlife. Whether it’s singing in a karaoke room, enjoying drinks at a lounge, or exploring adult entertainment venues, there’s plenty to see and do. Websites like 울산 풀사롱 (ulsanfullsalon.org) help navigate the city’s options so you can enjoy a memorable night in Ulsan.
BLOG
Request ID: The Complete Guide to Implementation, Debugging & Distributed Tracing
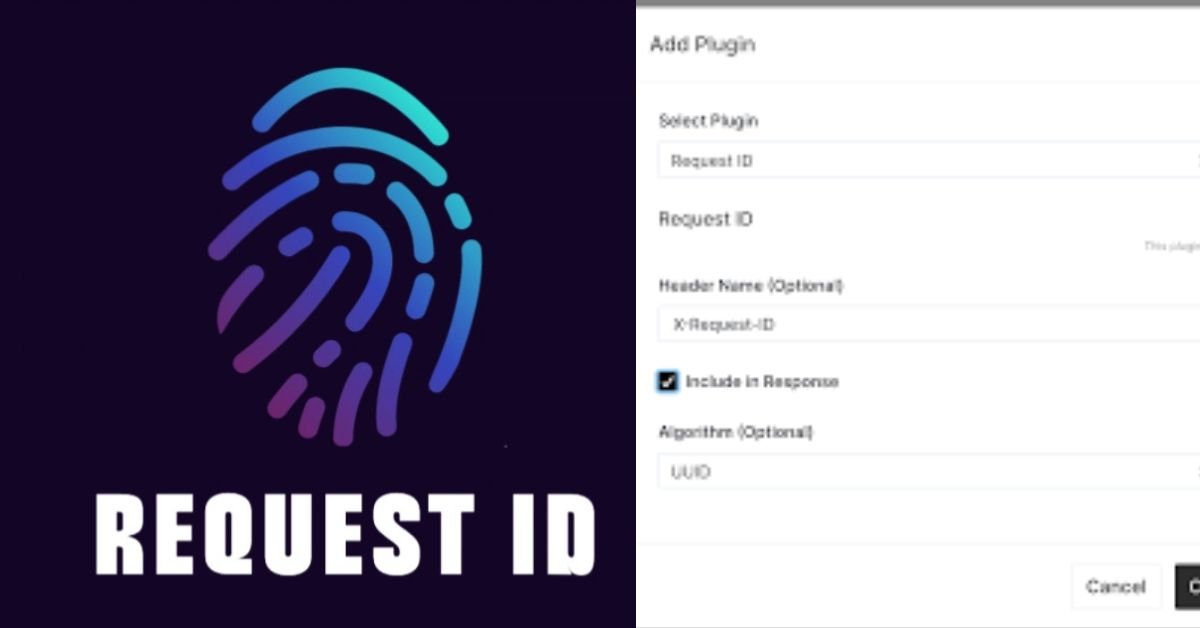
Request ID Debugging a production error without proper request tracking is like trying to find a specific conversation in a crowded room where everyone is talking at once. When multiple users experience issues simultaneously, isolating a single problematic transaction becomes nearly impossible. Request IDs solve this fundamental challenge by assigning a unique identifier to each HTTP request, creating a traceable thread through your entire application stack.
This comprehensive guide covers everything from basic implementation to advanced distributed tracing patterns, helping you reduce mean time to resolution (MTTR) by up to 70% while improving system observability and customer support efficiency.
What is a Request ID? Definition & Core Concepts
The Problem: Debugging Without Request Tracking
Consider this common scenario: Your monitoring system alerts you to a spike in 500 errors. You open the logs and see hundreds of error messages from the same timeframe. Which error belongs to which user? Which request triggered the cascade of failures? Without request tracking, engineers waste hours correlating timestamps, user agents, and IP addresses—often unsuccessfully.
The challenges multiply in modern architectures:
- Multiple concurrent requests from the same user
- Load-balanced servers processing overlapping transactions
- Microservices generating logs across distributed systems
- Asynchronous operations losing context across event boundaries
- Customer support teams unable to reference specific error instances
How Request IDs Solve Tracing Problems
A request ID is a unique identifier—typically a UUID (Universally Unique Identifier)—assigned to each incoming HTTP request. This identifier propagates through your entire request-response cycle, appearing in:
- Application logs at every processing stage
- HTTP response headers returned to clients
- Error messages and exception stack traces
- Monitoring system traces and metrics
- Database query logs and transaction records
- Message queue payloads and event streams
The request ID acts as a golden thread that ties together all activities related to a single user transaction. When an error occurs, engineers can search logs using the request ID to reconstruct the exact sequence of events, regardless of which servers or services were involved.
Request ID vs Correlation ID: Key Differences
While often used interchangeably, these terms have distinct meanings in distributed systems:
| Aspect | Request ID | Correlation ID |
| Scope | Single service/request | Multiple services/entire transaction |
| Lifespan | One HTTP request-response | Entire business transaction across services |
| Use Case | Debugging within one application | Tracing across microservices architecture |
Best Practice: In microservices environments, generate a correlation ID at the API gateway and a unique request ID for each internal service call. This creates both high-level transaction tracking and granular service-level debugging.
Key Benefits & Business Value of Request IDs
Accelerated Debugging & Reduced MTTR
Request IDs dramatically reduce the time engineers spend isolating and diagnosing issues. Industry data suggests teams implementing comprehensive request tracking see:
- 40-70% reduction in average debugging time
- 60% faster root cause analysis in distributed systems
- 80% improvement in first-time fix rate for production bugs
- Reduction in MTTR from hours to minutes for critical incidents
Instead of manually correlating timestamps and IP addresses across multiple log files, engineers simply grep for the request ID and immediately see the complete transaction timeline.
Enhanced User Experience & Support Efficiency
When users encounter errors, displaying the request ID creates a shared reference point between customers and support teams:
- Users can report “Error ID: abc-123” instead of vague descriptions
- Support agents instantly access relevant logs without interrogating users
- Reduced back-and-forth communication and faster resolution
- Professional appearance builds user confidence in your error handling
- Automated ticket systems can pre-populate context from request IDs
Example user-facing error:
“We are sorry, something went wrong. Please contact support with Error ID: 7f9a4e3c-2b1d-4a5e-8c3f-1e2d3c4b5a6f”
Distributed System Observability
In microservices architectures, a single user request might traverse a dozen services. Request IDs (combined with correlation IDs) enable:
- End-to-end transaction tracing across service boundaries
- Performance bottleneck identification at each service hop
- Dependency mapping and service interaction visualization
- Cascading failure analysis and circuit breaker optimization
- Integration with distributed tracing tools (Jaeger, Zipkin, OpenTelemetry)
Compliance & Audit Trail Creation
Request IDs create immutable audit trails for regulatory compliance:
- Financial services: PCI-DSS and SOC 2 audit requirements
- Healthcare: HIPAA-compliant activity logging
- E-commerce: Payment processing verification and dispute resolution
- Data privacy: GDPR/CCPA access request and deletion tracking
- Security incidents: Forensic investigation and breach analysis
Implementing Request IDs: Complete Technical Guide
HTTP Header Standards & Best Practices
While no official HTTP standard mandates specific headers, industry conventions have emerged:
| Header Name | Common Usage | Recommendation |
| X-Request-ID | Single service request tracking | Use for internal service requests |
| X-Correlation-ID | Multi-service transaction tracking | Use for end-to-end workflows |
| Request-ID | RFC-compliant alternative | Gaining adoption, more standard |
Convention: Always include the request ID in both the request headers (for propagation) and response headers (for client visibility). Many platforms like Heroku and AWS automatically add X-Request-ID headers.
Generating Effective Request IDs
UUID Version 4 (random) remains the most common choice for request IDs:
- Statistically unique without coordination: ~0% collision probability
- No sequential information leakage (unlike auto-incrementing IDs)
- Standard format: 550e8400-e29b-41d4-a716-446655440000
- Widely supported across all programming languages
- URL-safe and easily parseable
Alternative: UUID Version 7 (time-ordered) offers better database indexing performance for high-volume systems while maintaining uniqueness. Consider v7 if you store request IDs in indexed database columns.
Performance Note: UUID generation overhead is negligible (~1-2 microseconds). The performance impact of adding request IDs to headers and logs is unmeasurable in production systems.
Platform-Specific Implementation Guides
Node.js & Express Implementation
Express middleware provides the cleanest approach for request ID generation and propagation:
const express = require(‘express’);
const { v4: uuidv4 } = require(‘uuid’);
const app = express();
// Request ID middleware – place before all other middleware
app.use((req, res, next) => {
// Check for existing request ID (from upstream proxy/gateway)
const requestId = req.headers[‘x-request-id’] || uuidv4();
// Attach to request object for easy access
req.requestId = requestId;
// Add to response headers
res.setHeader(‘X-Request-ID’, requestId);
next();
});
// Custom logger that includes request ID
function log(req, level, message) {
console.log(JSON.stringify({
timestamp: new Date().toISOString(),
level: level,
requestId: req.requestId,
message: message
}));
}
// Example route using request ID
app.get(‘/api/users/:id’, async (req, res) => {
log(req, ‘info’, `Fetching user ${req.params.id}`);
try {
const user = await getUserById(req.params.id);
log(req, ‘info’, ‘User fetched successfully’);
res.json(user);
} catch (error) {
log(req, ‘error’, `Failed to fetch user: ${error.message}`);
res.status(500).json({
error: ‘Internal server error’,
requestId: req.requestId
});
}
});
app.listen(3000)
Python (Django/Flask) Implementation
Flask example with request context and structured logging:
from flask import Flask, request, g
import uuid
import logging
import json
app = Flask(__name__)
# Configure structured JSON logging
class RequestIdFilter(logging.Filter):
def filter(self, record):
record.request_id = getattr(g, ‘request_id’, ‘no-request-id’)
return True
logging.basicConfig(level=logging.INFO)
logger = logging.getLogger(__name__)
logger.addFilter(RequestIdFilter())
@app.before_request
def add_request_id():
# Check for existing request ID or generate new one
g.request_id = request.headers.get(‘X-Request-ID’, str(uuid.uuid4()))
@app.after_request
def add_request_id_header(response):
response.headers[‘X-Request-ID’] = g.request_id
return response
@app.route(‘/api/users/<user_id>’)
def get_user(user_id):
logger.info(f’Fetching user {user_id}’, extra={
‘request_id’: g.request_id,
‘user_id’: user_id
})
try:
user = fetch_user_from_db(user_id)
return {‘user’: user}
except Exception as e:
logger.error(f’Error fetching user: {str(e)}’, extra={
‘request_id’: g.request_id,
‘user_id’: user_id
})
return {‘error’: ‘Internal server error’, ‘requestId’: g.request_id}, 500
if __name__ == ‘__main__’:
app.run()
Django Implementation: Create custom middleware in middleware.py and add request ID to the LogRecord using a filter, similar to the Flask example above.
Java Spring Boot Implementation
Spring Boot uses filters and MDC (Mapped Diagnostic Context) for thread-local request tracking:
import org.slf4j.MDC;
import javax.servlet.*;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
import java.util.UUID;
@Component
@Order(Ordered.HIGHEST_PRECEDENCE)
public class RequestIdFilter implements Filter {
private static final String REQUEST_ID_HEADER = “X-Request-ID”;
@Override
public void doFilter(ServletRequest request, ServletResponse response,
FilterChain chain) throws IOException, ServletException {
HttpServletRequest httpRequest = (HttpServletRequest) request;
HttpServletResponse httpResponse = (HttpServletResponse) response;
// Get or generate request ID
String requestId = httpRequest.getHeader(REQUEST_ID_HEADER);
if (requestId == null || requestId.isEmpty()) {
requestId = UUID.randomUUID().toString();
}
// Store in MDC for logging
MDC.put(“requestId”, requestId);
// Add to response headers
httpResponse.setHeader(REQUEST_ID_HEADER, requestId);
try {
chain.doFilter(request, response);
} finally {
// Always clear MDC to prevent thread-local leaks
MDC.clear();
}
}
}
// Configure logback.xml to include MDC values:
// <pattern>%d{ISO8601} [%thread] %-5level %logger{36} [%X{requestId}] – %msg%n</pattern>
.NET Core Implementation
.NET Core middleware with ILogger integration:
using Microsoft.AspNetCore.Http;
using System;
using System.Threading.Tasks;
public class RequestIdMiddleware
{
private readonly RequestDelegate _next;
private const string RequestIdHeader = “X-Request-ID”;
public RequestIdMiddleware(RequestDelegate next)
{
_next = next;
}
public async Task InvokeAsync(HttpContext context)
{
// Get or generate request ID
var requestId = context.Request.Headers[RequestIdHeader].FirstOrDefault()
?? Guid.NewGuid().ToString();
// Store in HttpContext.Items for access throughout request
context.Items[“RequestId”] = requestId;
// Add to response headers
context.Response.Headers[RequestIdHeader] = requestId;
// Add to logging scope
using (_logger.BeginScope(new Dictionary<string, object>
{
[“RequestId”] = requestId
}))
{
await _next(context);
}
}
}
// Register in Startup.cs:
// app.UseMiddleware<RequestIdMiddleware>();
// Access in controllers:
var requestId = HttpContext.Items[“RequestId”]?.ToString();
Passing Request IDs Across Service Boundaries
In distributed systems, request IDs must propagate through all service-to-service communications:
HTTP Client Configuration:
// Node.js example – propagate request ID to downstream services
const axios = require(‘axios’);
async function callDownstreamService(requestId, userId) {
const response = await axios.get(`https://user-service/api/users/${userId}`, {
headers: {
‘X-Request-ID’: requestId,
‘X-Correlation-ID’: requestId // if no separate correlation ID exists
}
});
return response.data;
}
Message Queue Pattern: When using message queues (RabbitMQ, Kafka, SQS), include request/correlation IDs in message headers or metadata fields to maintain traceability across asynchronous operations.
Logging & Monitoring Integration
Structured Logging with Request Context
Structured logging in JSON format enables powerful log aggregation and analysis:
{
“timestamp”: “2026-02-06T15:23:45.123Z”,
“level”: “error”,
“requestId”: “7f9a4e3c-2b1d-4a5e-8c3f-1e2d3c4b5a6f”,
“correlationId”: “a1b2c3d4-e5f6-7890-abcd-ef1234567890”,
“service”: “user-service”,
“userId”: “12345”,
“message”: “Database query timeout”,
“stack”: “Error: Query timeout\n at Database.query…”,
“metadata”: {
“query”: “SELECT * FROM users WHERE id = ?”,
“duration_ms”: 5000
}
}
Benefits of structured logging with request IDs:
- Query logs by request ID to see complete transaction timeline
- Aggregate error rates by correlation ID to identify systemic issues
- Filter logs by service + request ID for microservice debugging
- Automated alerting based on error patterns within request flows
- Machine learning analysis of request patterns and anomalies
Integrating with Observability Platforms
Modern observability tools automatically extract and index request IDs:
| Platform | Request ID Support | Key Features |
| OpenTelemetry | Native trace/span ID support | Industry standard, vendor-neutral |
| Datadog | Automatic extraction from logs | APM integration, distributed tracing |
| New Relic | Request ID correlation | Full-stack observability, error tracking |
| Grafana/Loki | LogQL label queries | Open-source, powerful visualization |
OpenTelemetry Integration: OpenTelemetry represents the future of request tracking, providing standardized APIs for distributed tracing. Request IDs map to trace IDs and span IDs in the OpenTelemetry model.
Creating Effective Dashboards & Alerts
Leverage request IDs to build powerful monitoring dashboards:
- Request flow visualization: trace paths through microservices
- Error rate trends: group by correlation ID to identify systemic failures
- Performance histograms: analyze latency distributions per service
- Dependency graphs: map service interactions automatically
- Real-time alerts: trigger on specific request ID patterns
Example Query (Grafana/Loki):
{service=”api-gateway”} |= “requestId” | json | requestId=”7f9a4e3c-2b1d-4a5e-8c3f-1e2d3c4b5a6f”
Advanced Patterns & Considerations
High-Performance Systems & Scaling Considerations
Request IDs introduce minimal overhead, but optimization matters at scale:
- UUID generation: ~1-2 microseconds (negligible impact)
- Header overhead: 50-100 bytes per request (0.0001% of typical payloads)
- Logging overhead: Use asynchronous logging to prevent I/O blocking
- Database indexing: Index request ID columns if querying frequently
- Cache warming: Pre-generate UUIDs in high-throughput systems (rarely needed)
Benchmark Data: Adding request ID middleware to a Node.js application processing 10,000 requests/second adds <0.1ms latency on average—well within acceptable performance budgets.
Security & Privacy Considerations
Request IDs can inadvertently expose information or create security risks:
| Risk | Mitigation Strategy |
| Sequential IDs reveal request volume | Use random UUIDs, not auto-incrementing IDs |
| Request IDs in URLs enable enumeration | Never use request IDs as primary identifiers in URLs |
| PII leakage in logs | Sanitize logs; avoid logging sensitive data with request IDs |
| GDPR/CCPA compliance | Implement log retention policies; enable request ID-based deletion |
GDPR Consideration: Request IDs themselves are not personal data, but logs containing request IDs may include PII. Ensure your log retention and deletion processes can purge all data associated with a specific request ID.
Legacy System Integration Strategies
Adding request IDs to existing systems without breaking functionality:
- Proxy-based approach: Add reverse proxy (Nginx/HAProxy) to inject request IDs
- Gradual rollout: Implement in new services first, propagate to legacy systems
- Backward compatibility: Make request ID headers optional; generate if missing
- Database triggers: Auto-populate request ID columns with defaults for legacy rows
- Feature flags: Toggle request ID functionality per environment
Industry-Specific Implementations
Different industries have unique requirements for request tracking:
Financial Services: PCI-DSS compliance requires detailed audit trails. Request IDs must be immutable, tamper-evident, and retained for 1+ years. Integration with SIEM systems (Splunk, QRadar) is standard.
Healthcare: HIPAA audit controls mandate tracking all access to PHI (Protected Health Information). Request IDs link user actions to specific medical records, enabling compliance reporting and breach investigation.
E-commerce: Payment processing errors require request IDs to reconcile transactions with payment gateways (Stripe, PayPal). Include request ID in order confirmation emails for customer service efficiency.
Real-World Troubleshooting Scenarios
Step-by-Step Debugging Workflow
How to leverage request IDs for efficient debugging:
1. Capture the Request ID – User reports error; obtain request ID from error message or response headers
2. Search Centralized Logs – Query: grep “7f9a4e3c-2b1d-4a5e-8c3f-1e2d3c4b5a6f” /var/log/app/*.log
3. Reconstruct Timeline – Sort log entries by timestamp; identify sequence of service calls
4. Identify Failure Point – Look for error-level logs, exceptions, or missing expected log entries
5. Check Upstream/Downstream – Trace correlation ID to see related requests in other services
6. Verify Fix – Reproduce issue; confirm new request ID shows expected behavior
Common Pitfalls & How to Avoid Them
| Pitfall | Solution |
| Request IDs not propagating to downstream services | Ensure all HTTP clients include X-Request-ID header |
| Logging request IDs but not including in errors | Add request ID to all error responses and exceptions |
| Request ID collisions (duplicate IDs) | Use UUID v4; verify generation library is cryptographically random |
| Missing request IDs in asynchronous operations | Pass request ID as function parameter or use async context |
Case Study: Reducing Debug Time by 65%
A mid-sized SaaS company with a microservices architecture implemented comprehensive request tracking:
Before Implementation:
- Average debugging time: 2.5 hours per production incident
- Customer support resolution: 4-6 hours
- Root cause identification rate: 60% (40% remained unresolved)
After Implementation:
- Average debugging time: 45 minutes (65% reduction)
- Customer support resolution: 1.5 hours
- Root cause identification rate: 95%
- Additional benefit: Automated error categorization and routing
Key Success Factors: Consistent implementation across all 12 microservices, integration with Datadog for centralized logging, and user-facing error IDs that created shared context between customers and support teams.
Frequently Asked Questions
Q: How do I generate a unique request ID in my specific language/framework?
A: Most modern languages have UUID libraries built-in or readily available:
JavaScript: require(‘uuid’).v4()
Python: import uuid; uuid.uuid4()
Java: UUID.randomUUID().toString()
C#: Guid.NewGuid().ToString()
Ruby: SecureRandom.uuid
Go: github.com/google/uuid package
PHP: uniqid() or ramsey/uuid library
Q: Should request IDs be exposed to end users?
A: Yes, displaying request IDs in error messages significantly improves support efficiency. Users can reference specific error instances when reporting issues. However, never use request IDs as authorization tokens or expose them in a way that enables system enumeration.
Q: What is the difference between X-Request-ID and X-Correlation-ID?
A: X-Request-ID typically identifies a single HTTP request to one service. X-Correlation-ID spans the entire business transaction across multiple services. In practice, many teams use them interchangeably for simpler architectures.
Q: How do I pass request IDs between microservices?
A: Include the request ID as an HTTP header (X-Request-ID or X-Correlation-ID) in all inter-service HTTP requests. For message queues, add it to message metadata. For event streams, include it in the event payload.
Q: How can request IDs help reduce our mean time to resolution (MTTR)?
A: Request IDs eliminate the manual correlation work that consumes 60-80% of debugging time. Engineers can immediately retrieve the complete transaction timeline, identify the failure point, and trace dependencies—reducing MTTR from hours to minutes.
Q: What logging format works best with request IDs?
A: Structured JSON logging enables powerful querying and analysis. Include request ID as a top-level field in every log entry. This enables filtering, aggregation, and visualization in modern log management tools.
Q: Do request IDs impact application performance?
A: The performance impact is negligible. UUID generation takes 1-2 microseconds. Header overhead is ~100 bytes per request. In benchmarks, request ID middleware adds <0.1ms latency—well within acceptable performance budgets.
Q: How do I convince my team to implement request IDs?
A: Focus on the business impact: 40-70% reduction in debugging time, faster customer support resolution, compliance benefits, and improved system observability. Start with a pilot implementation in one service to demonstrate value before rolling out organization-wide.
Q: What are alternatives to request IDs for distributed tracing?
A: OpenTelemetry provides comprehensive distributed tracing with trace contexts, spans, and baggage. Commercial solutions include Datadog APM, New Relic, Dynatrace, and Jaeger. However, request IDs remain the simplest, lowest-overhead solution for basic debugging needs.
Q: How do request IDs fit into our compliance requirements?
A: Request IDs create immutable audit trails required by PCI-DSS, HIPAA, SOC 2, and other frameworks. They enable forensic investigation of security incidents, demonstrate access controls, and provide evidence of proper data handling. Ensure logs with request IDs meet retention requirements (typically 1-7 years depending on industry).
Conclusion: Implementing Request IDs for Long-Term Success
Request IDs represent a fundamental shift from reactive debugging to proactive observability. By implementing comprehensive request tracking, organizations gain:
- Dramatic reduction in mean time to resolution (40-70% improvement)
- Enhanced customer experience through faster support resolution
- Compliance audit trails for regulatory requirements
- Foundation for advanced distributed tracing and observability
- Data-driven insights into system behavior and user patterns
Start with a simple implementation in your most critical services, validate the benefits with metrics, then expand to your entire stack. The minimal development effort—typically 1-2 days for comprehensive implementation—delivers outsized returns in debugging efficiency, system reliability, and team productivity.
-

 ENTERTAINMENT7 months ago
ENTERTAINMENT7 months agoTesla Trip Planner: Your Ultimate Route and Charging Guide
-

 BUSNIESS7 months ago
BUSNIESS7 months agoCareers with Impact: Jobs at the Australian Services Union
-

 TECHNOLOGY7 months ago
TECHNOLOGY7 months agoFaceTime Alternatives: How to Video Chat on Android
-

 BLOG7 months ago
BLOG7 months agoCamel Toe Explained: Fashion Faux Pas or Body Positivity?
-

 FASHION7 months ago
FASHION7 months agoWrist Wonders: Handcrafted Bracelet Boutique
-

 BUSNIESS6 months ago
BUSNIESS6 months agoChief Experience Officer: Powerful Driver of Success
-

 ENTERTAINMENT7 months ago
ENTERTAINMENT7 months agoCentennial Park Taylor Swift: Where Lyrics and Nashville Dreams Meet
-

 BLOG7 months ago
BLOG7 months agoStep Into Rewards: The Nike Credit Card Advantage
